The use of deploying a Host-based Intrusion Detection System (HIDS) agent for an AlienVault Appliance is to enhance the security monitoring capabilities of the system by providing detailed visibility into the activities and events occurring on individual hosts or endpoints.
HIDS agents are installed on individual systems and continuously monitor the system’s activities, including file integrity, log analysis, and system behavior. When integrated with an AlienVault Appliance, the HIDS agents can send the collected data and alerts to the central AlienVault server for analysis and correlation with other security events.
Here are some key benefits and use cases of deploying HIDS agents for AlienVault Appliance:
- Threat Detection and Incident Response: HIDS agents monitor the system for suspicious activities, unauthorized access attempts, malware infections, and other indicators of compromise. By deploying HIDS agents across multiple endpoints, organizations can detect and respond to security incidents in real-time, allowing for quick mitigation and containment.
- File Integrity Monitoring: HIDS agents can monitor critical system files and directories for any unauthorized modifications or tampering. If any changes occur, the agent can generate alerts, helping organizations detect potential security breaches or insider threats.
- Log Analysis and Event Correlation: HIDS agents collect and analyze logs generated by various system components, such as operating systems, applications, and network devices. These logs provide valuable information for detecting security incidents, identifying patterns, and correlating events across the enterprise. By centralizing the log data on the AlienVault Appliance, organizations can gain comprehensive visibility into their IT infrastructure and identify potential security threats.
- Compliance Monitoring: HIDS agents can assist organizations in meeting compliance requirements by continuously monitoring systems for configuration changes, user activities, and other parameters defined by regulatory standards. The collected data can be used to generate reports and demonstrate adherence to security policies and industry regulations.
- Endpoint Visibility: HIDS agents provide detailed visibility into the activities and behaviors of individual endpoints, allowing security teams to identify any unusual or suspicious activities at a granular level. This information is particularly valuable in investigating and responding to security incidents, as it provides insight into the affected system’s state and potential attack vectors.
By deploying HIDS agents for an AlienVault Appliance, organizations can strengthen their overall security posture, enhance threat detection capabilities, and improve incident response processes by having comprehensive visibility into the activities occurring on their endpoints.
HIDS Agent Deployment on Linux
To deploy AlienVault HIDS agent (OSSEC) for Linux, you can follow these general steps:
- Download the HIDS Agent:
- Visit the OSSEC project website to download the HIDS agent package suitable for your Linux distribution. (Latest packages and instruction can be found in Alienvault / OSSEC website.
- The below Instructions are for Ubuntu.
# Add Apt sources.lst
wget -q -O - https://updates.atomicorp.com/installers/atomic | bash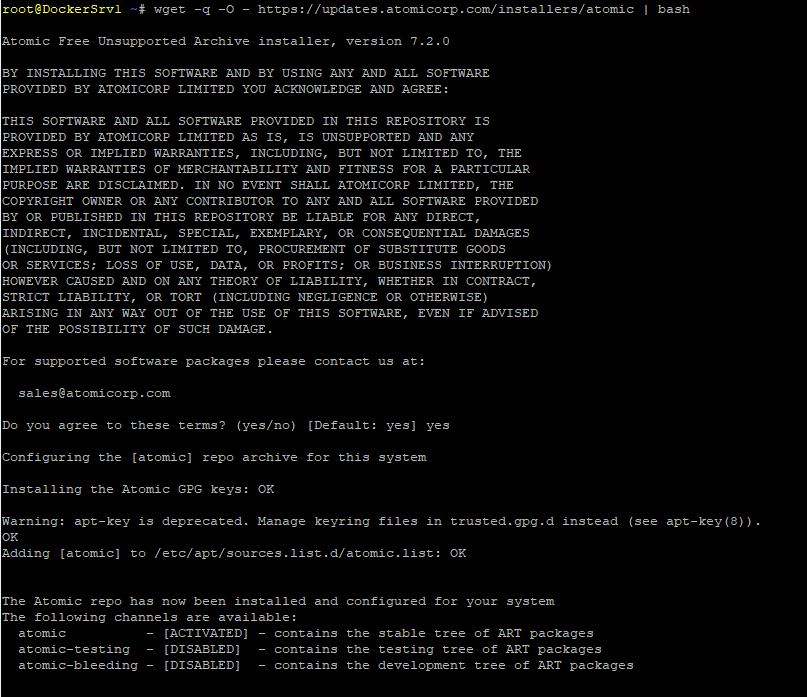
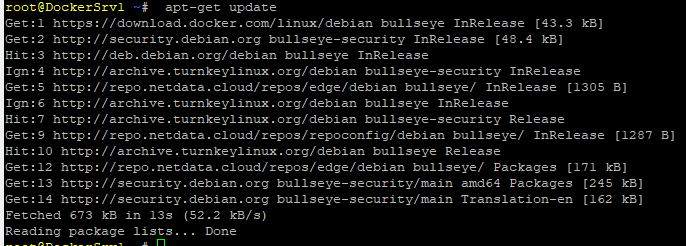
# Update apt data
apt-get update
# Agent
sudo apt-get install ossec-hids-agent
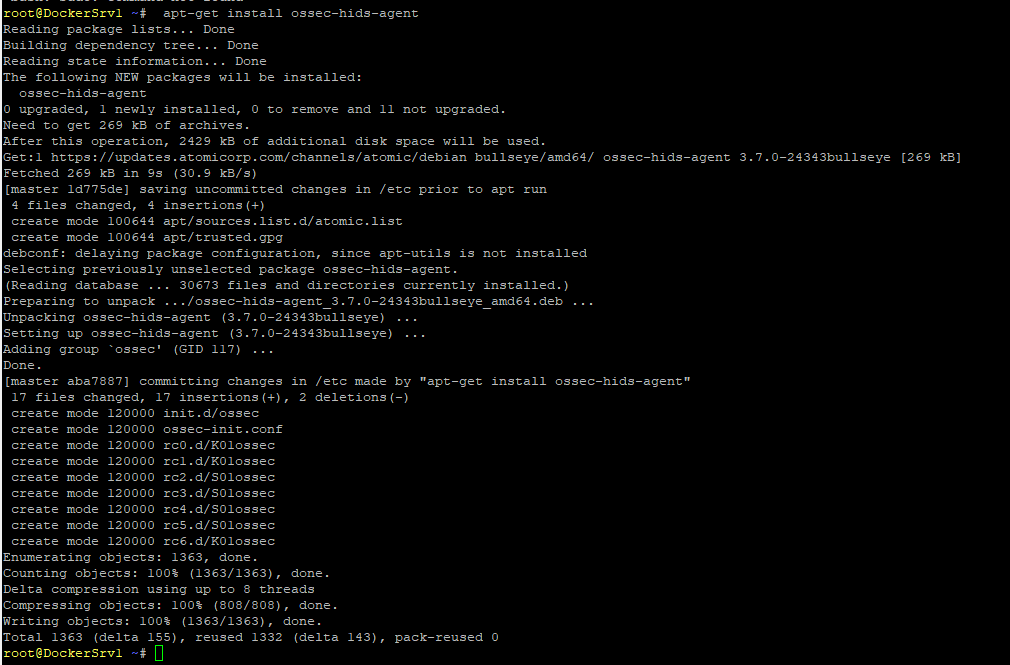
To Generate Unique Key for each HIDS Agent
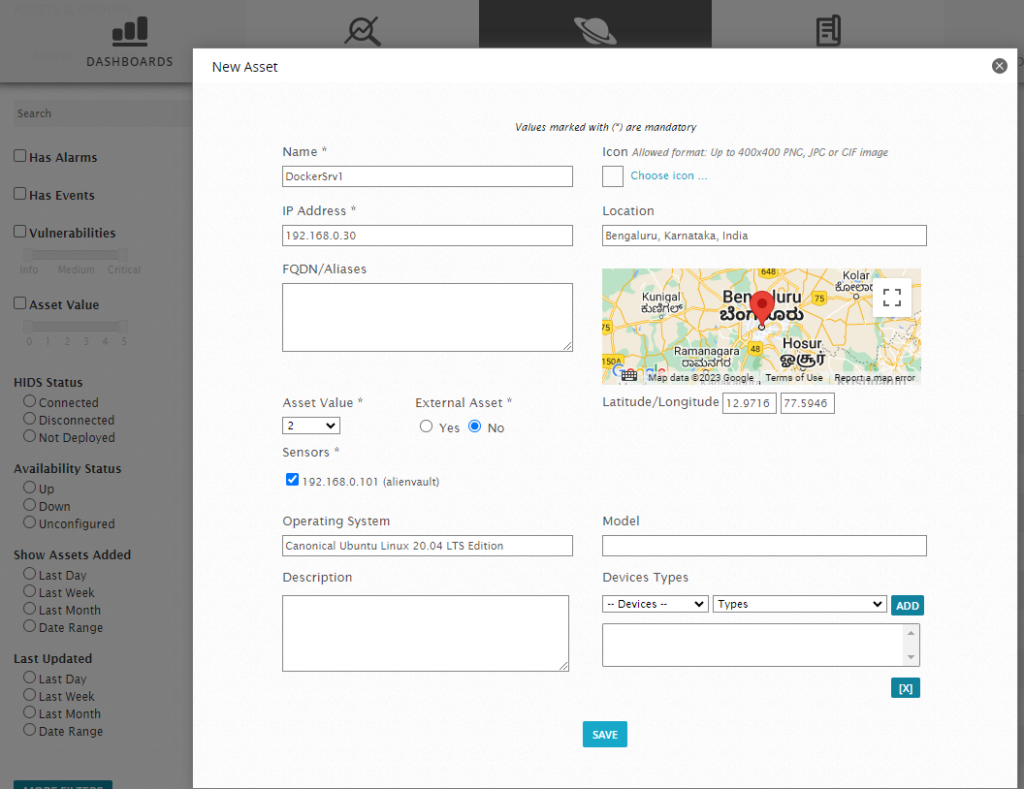
Add the Linux Server to SIEM incase not already added
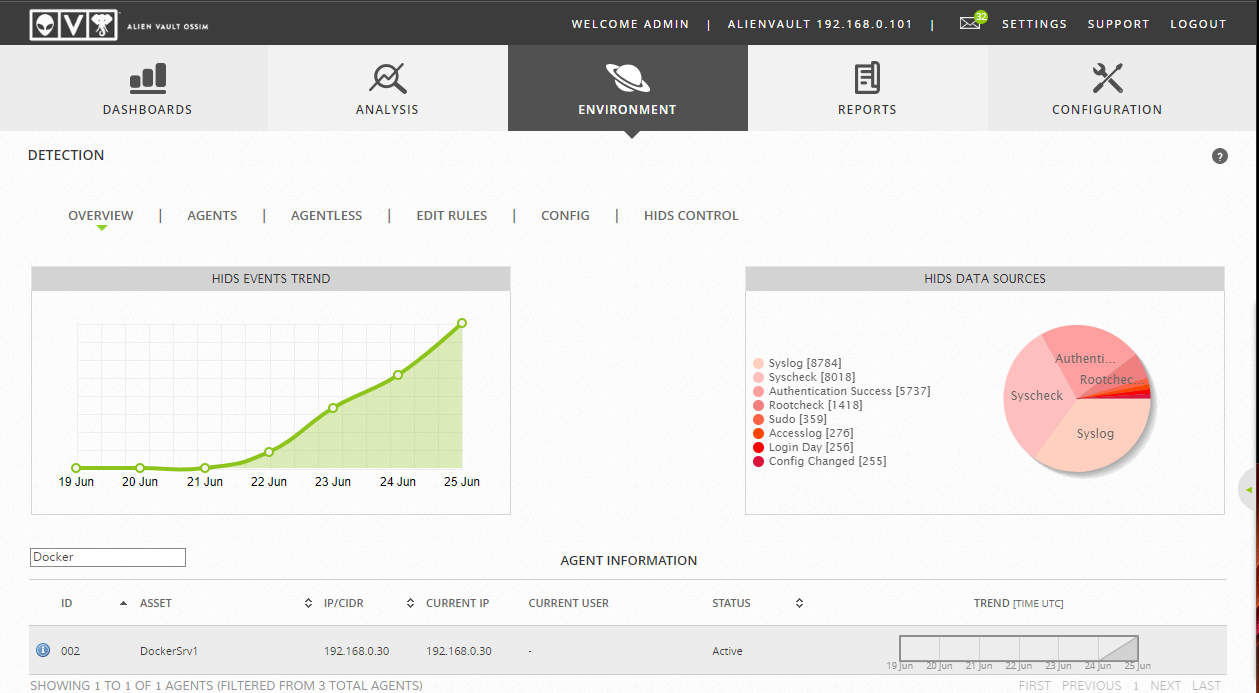
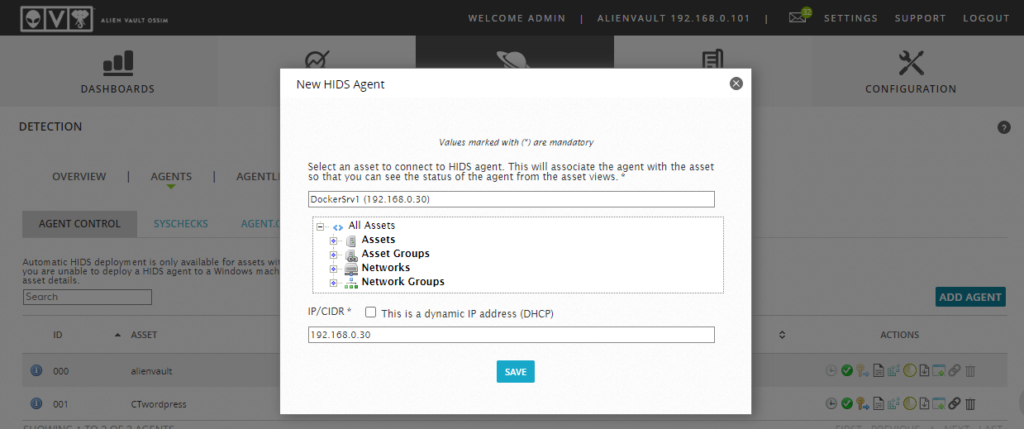
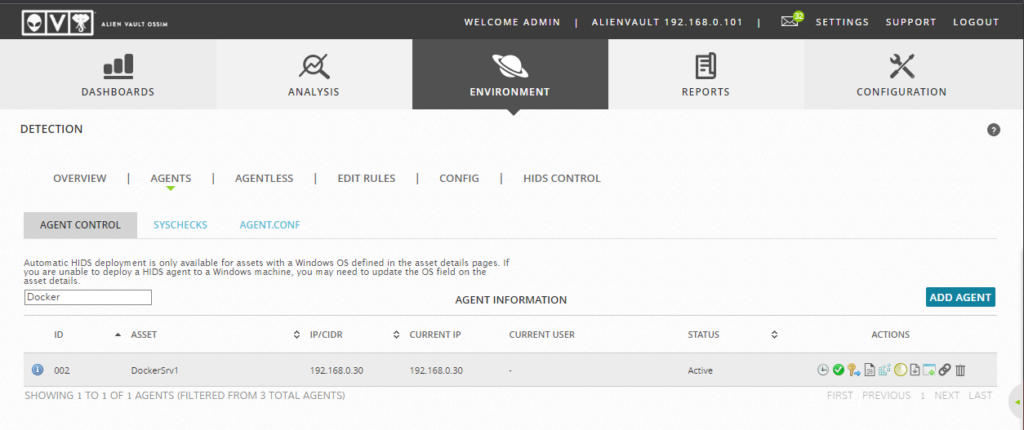
Add a Agent by Clicking “Add Agent” option under > Environment > Detection > Agents > Add Agent > Select the Asset which we have already added in previous step.
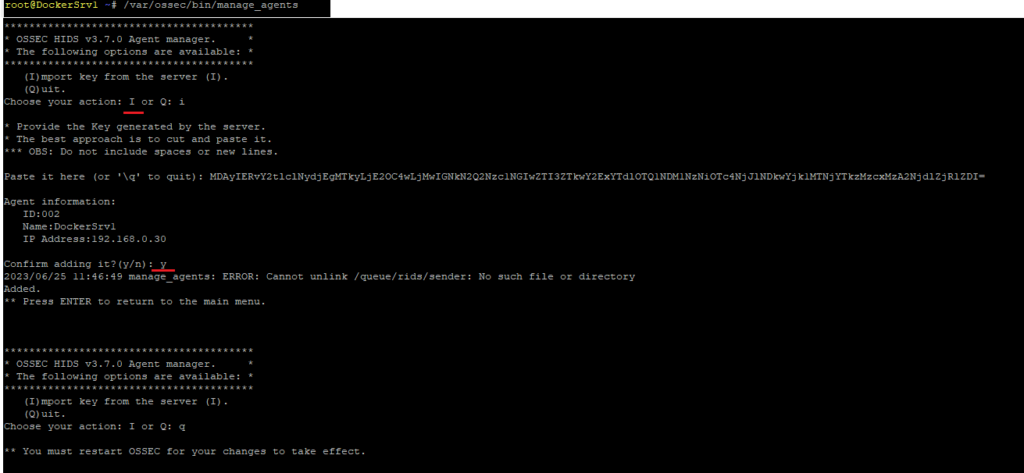
Select Extract Key option and copy the generated key.
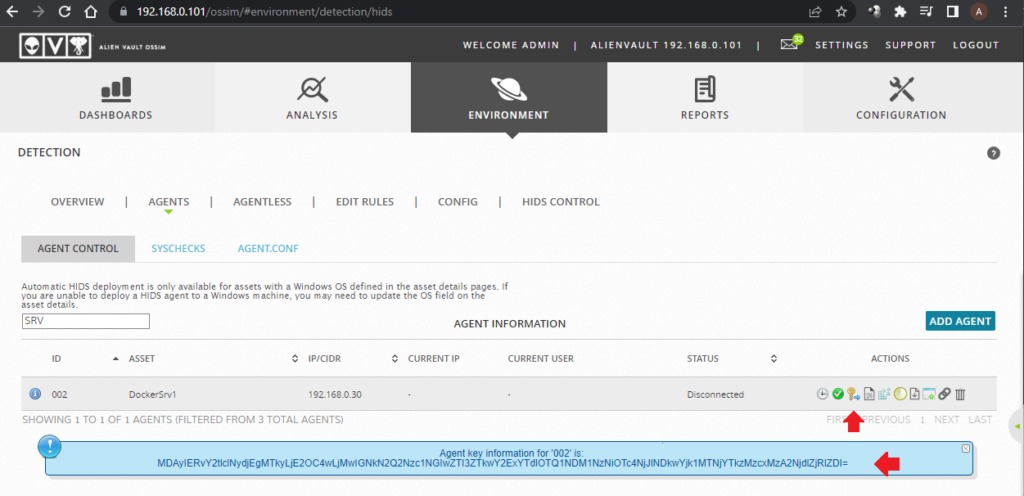
To import the key to Linux Machine
root@DockerSrv1 ~# /var/ossec/bin/manage_agents
Choose “I” to import
Edit Ossec agent config file located at
nano /var/ossec/etc/ossec.conf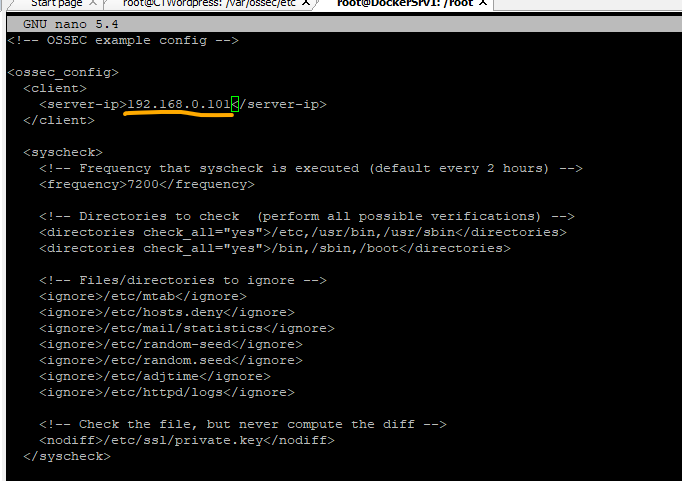
CTRL + O to save the file if using nano editor
and CTRL + X to exit
To Start HIDS agent
service ossec start
chkconfig ossec-hids on
Restart HIDS
OSSIM > Environment > Detection, click HIDS Control, and then Restart.
If the Key was entered correctly and all steps followed correct, Agent status should show as Active now
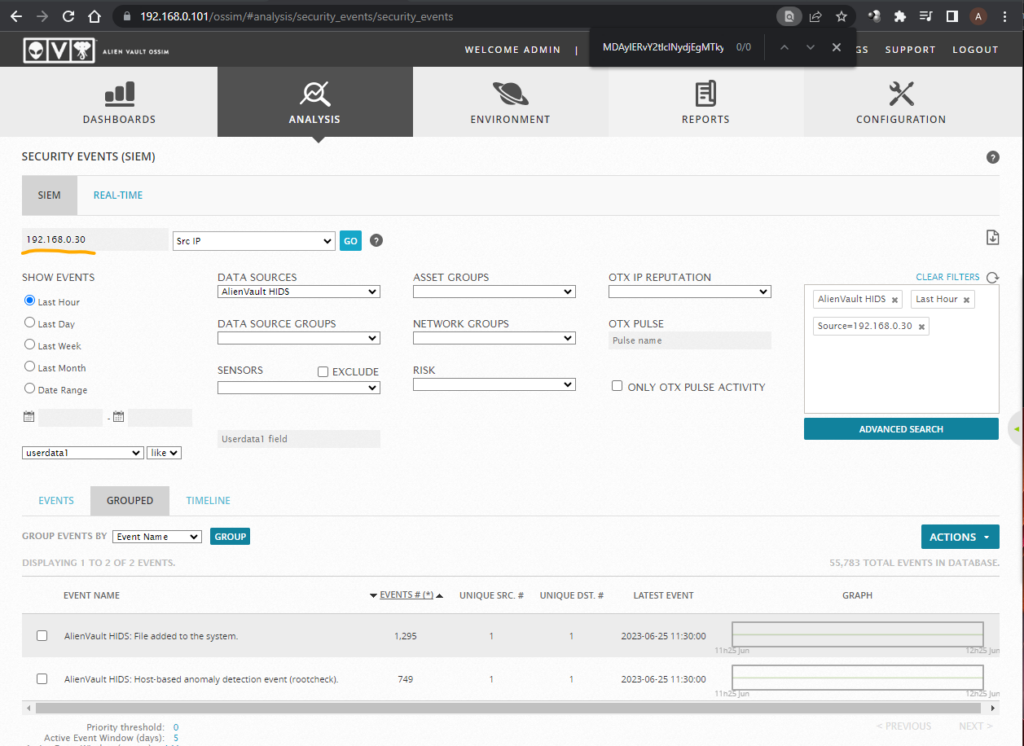
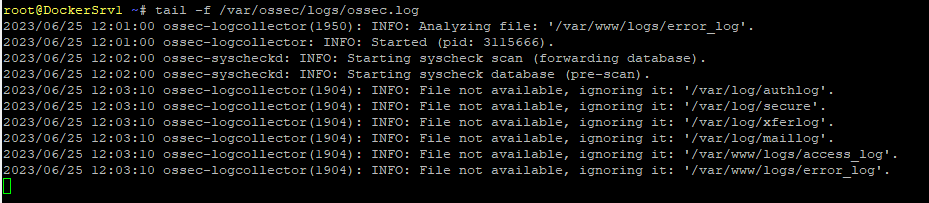
To View logs from the server
Analysis > SIEM > Enter the IP of server in below highlighted search area and criteria “Src IP”