Understanding T-Pot Honeypot: A Comprehensive Cybersecurity Tool
In the ever-evolving landscape of cybersecurity, honeypots play a crucial role in detecting and analyzing malicious activities. One of the most comprehensive and widely-used honeypot frameworks today is T-Pot. Developed and maintained by the German cybersecurity organization, Deutsche Telekom AG, T-Pot is an open-source honeypot system that provides an extensive set of tools for tracking and analyzing cyber threats.
What is T-Pot?
T-Pot is a multi-honeypot platform that integrates several open-source honeypot technologies into one cohesive system. The platform is designed to capture a wide range of attacks, from brute force attempts to sophisticated exploits. By simulating vulnerable systems, T-Pot attracts attackers and logs their activities, providing valuable insights into the tactics, techniques, and procedures (TTPs) used by threat actors.
Key Features of T-Pot
- Multi-Honeypot Deployment: T-Pot includes various honeypots such as Cowrie (SSH/Telnet), Dionaea (SMB/HTTP/FTP), and many others, making it a versatile tool for monitoring different types of attacks.
- Dockerized Environment: Each honeypot within T-Pot runs in its own Docker container, ensuring isolation and easy management of services. This setup also allows for quick deployment and scalability.
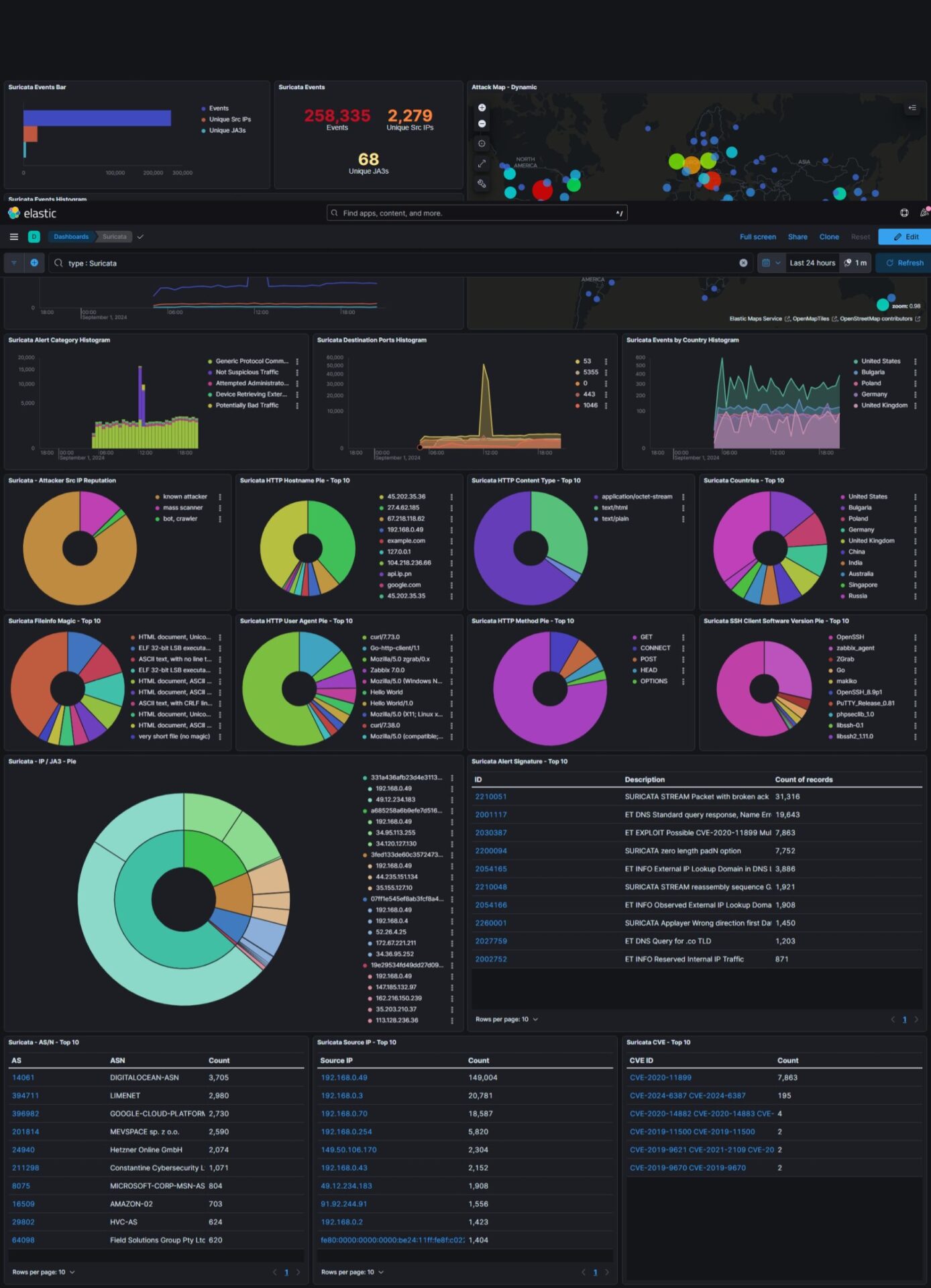
- Data Visualization: T-Pot comes with a built-in ELK (Elasticsearch, Logstash, Kibana) stack, which provides powerful data visualization capabilities. Users can easily analyze captured data, identify trends, and generate reports.
- Community and Support: As an open-source project, T-Pot has a strong community of developers and cybersecurity professionals who contribute to its development and provide support. This ensures that T-Pot remains up-to-date with the latest threat intelligence and security practices.
Why Use T-Pot?
Deploying T-Pot in your network can provide numerous benefits:
- Threat Intelligence: By capturing and analyzing attacks, T-Pot helps organizations stay informed about the latest threats targeting their systems.
- Incident Response: The detailed logs generated by T-Pot can be invaluable for incident response teams, providing a clear view of the attack vector and helping to mitigate the threat.
- Research and Development: T-Pot is an excellent tool for cybersecurity researchers who want to study attacker behavior and develop new defense strategies.
Conclusion
In an age where cyber threats are becoming increasingly sophisticated, tools like T-Pot are essential for proactive cybersecurity. Whether you are a seasoned security professional or a researcher, T-Pot offers a comprehensive solution for understanding and mitigating the threats that lurk in the digital world.
Referebce
T-Pot (github.com)
GitHub – telekom-security/tpotce: 🍯 T-Pot – The All In One Multi Honeypot Platform 🐝
Installation
System Requirement
RAM - 8-16GB
Disk - 128GB
Minimum: (Ref GitHub - telekom-security/tpotce: 🍯 T-Pot - The All In One Multi Honeypot Platform 🐝)Install Supported version of the OS GitHub – telekom-security/tpotce: 🍯 T-Pot – The All In One Multi Honeypot Platform 🐝
Install dependency such as curl (i have installed few non-essential packages such as htop, iotop)
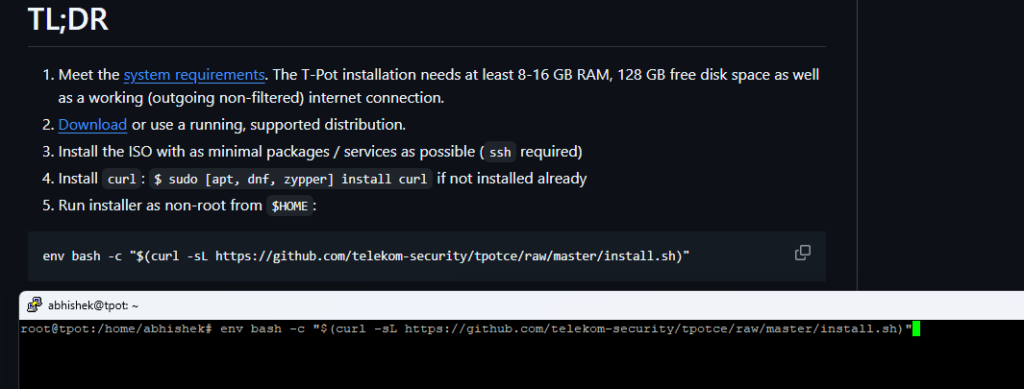
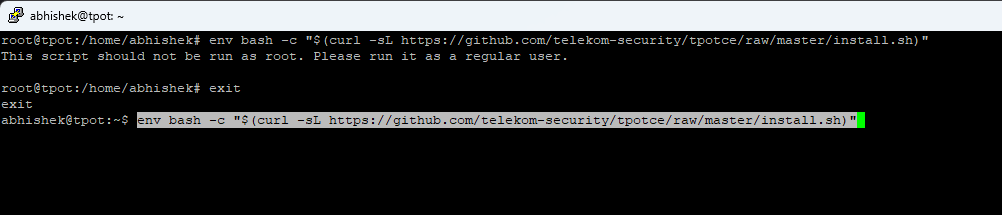
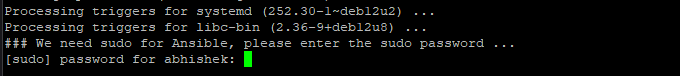
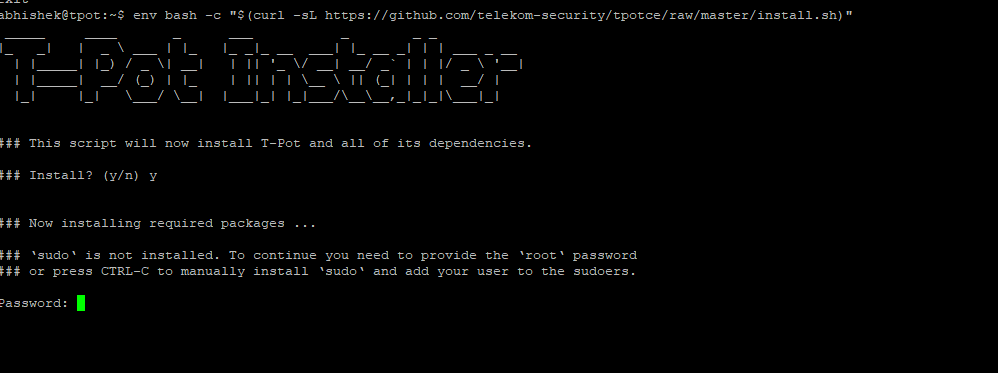
Incase ansible is giving error with locale, edit below file and add UTF Locale as mentioned below)
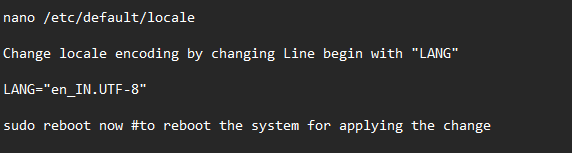
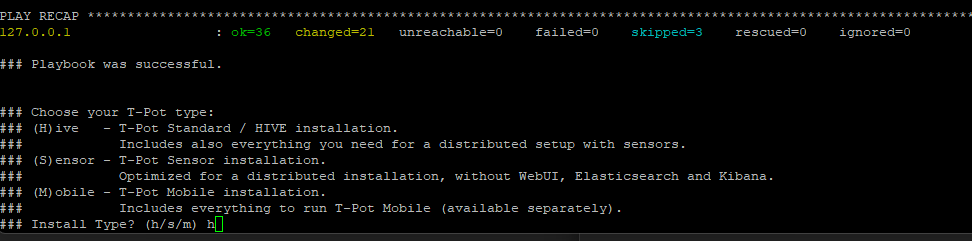
Select the T-POT type to install
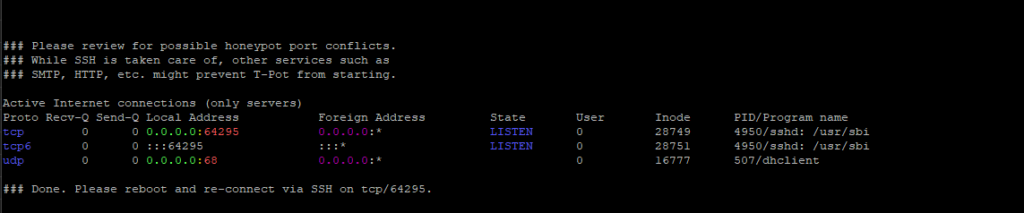
Management Console

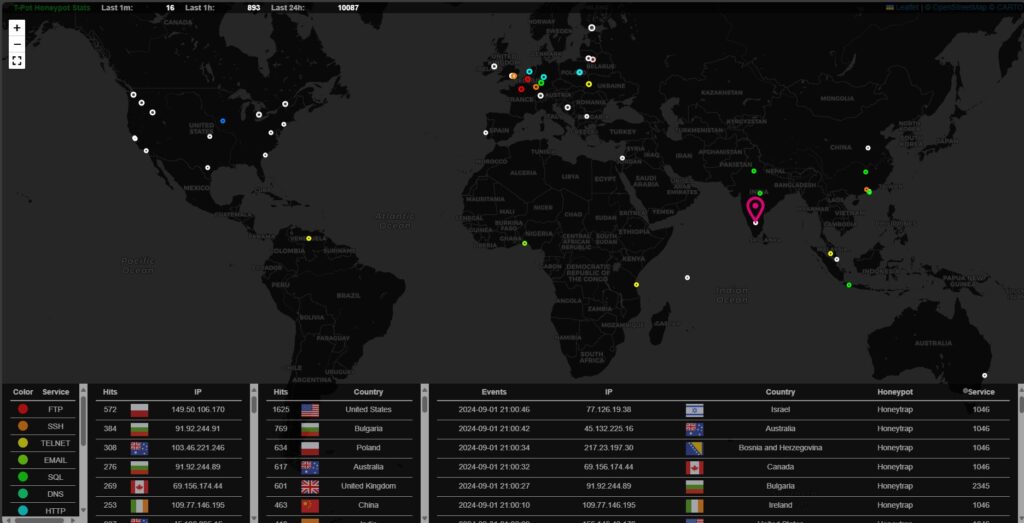
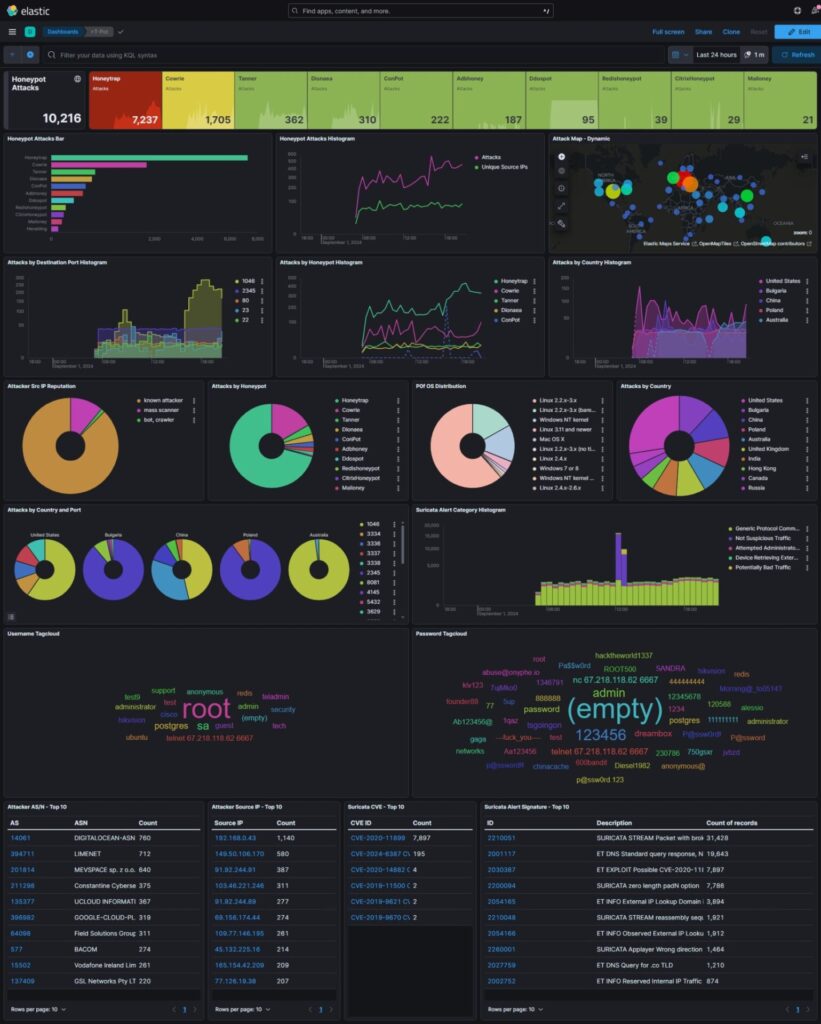
TPot > Suricata Dashboard